SmartFusion2 Secure Boot Solution From Microsemi
Microsemi Corporation announced it has completed differential power analysis (DPA) testing on its secure boot field programmable gate array (FPGA) solution, which resolves side channel vulnerabilities inherent in the configuration process of large static random-access memory (SRAM) FPGAs. The DPA testing was completed using the Test Vector Leakage Assessment (TVLA) methodology developed by Cryptography Research Incorporated (CRI), a division of Rambus. Results of the testing show Microsemi’s secure boot solution has sufficient design margin to protect against side channel attacks. TVLA was developed to address the shortcomings of evaluation-based testing in this field. Rather than focusing on key extraction, which may depend heavily on the expertise of the evaluator, TVLA is based on a statistical approach to derive an objective pass/fail score on the underlying system’s information leakage.
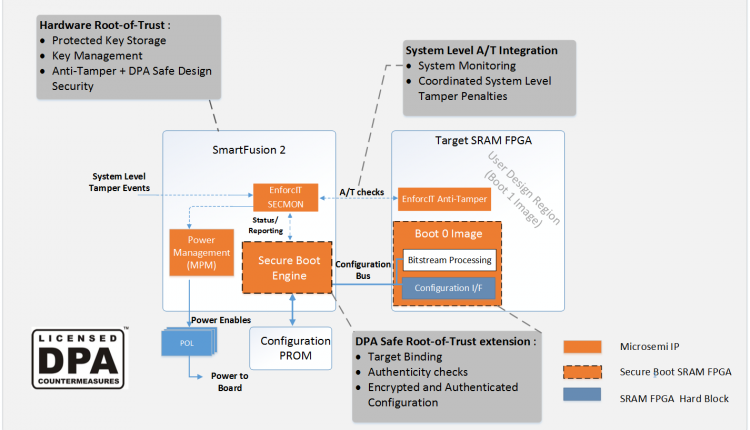
 Microsemi’s secure boot SRAM FPGA reference design is ideal for systems with requirements for high value intellectual property (IP) protection, including mitigations against side-channel attacks. Key applications include protection of high value commercial and critical infrastructure systems from cloning and reverse engineering. All commercially available SRAM FPGAs on the market today are susceptible to DPA and other related side-channel attacks, which can expose the bitstream decryption key and risk loss of valuable IP. Microsemi’s secure boot FPGA solution uses the company’s SmartFusion2 system-on-chip (SoC) FPGA to securely load target SRAM FPGAs, with all cryptographic processing performed in a DPA-safe manner. All cryptographic processing IP in the solution includes pass-through licenses from CRI for both the SmartFusion2 host and target FPGA platforms.
Microsemi’s secure boot SRAM FPGA reference design is ideal for systems with requirements for high value intellectual property (IP) protection, including mitigations against side-channel attacks. Key applications include protection of high value commercial and critical infrastructure systems from cloning and reverse engineering. All commercially available SRAM FPGAs on the market today are susceptible to DPA and other related side-channel attacks, which can expose the bitstream decryption key and risk loss of valuable IP. Microsemi’s secure boot FPGA solution uses the company’s SmartFusion2 system-on-chip (SoC) FPGA to securely load target SRAM FPGAs, with all cryptographic processing performed in a DPA-safe manner. All cryptographic processing IP in the solution includes pass-through licenses from CRI for both the SmartFusion2 host and target FPGA platforms.
“Microsemi’s secure boot solution ensures confidentiality and authentication of an underlying system design by leveraging the high security of our SmartFusion2 SoC FPGAs as a root-of-trust,” said Paul Quintana, director of vertical marketing for defense, security and computing at Microsemi. “Having a strong root-of-trust is often a critical element to protect and assure a design has not been modified.”
This technology is ideal for the defense and security market, as defense-grade systems often have requirements for anti-tamper to protect against reverse engineering of the underlying technology. This is a crucial requirement, especially for systems purposed for foreign military sales (FMS). Microsemi is currently engaged with leading defense contractors to implement this technology.
According to Strategy Analytics, global spending on RF-based electronic warfare (EW) systems is forecast to grow to more than $9.3 billion through 2022. The Strategy Analytics Advanced Defense Systems (ADS) service forecast model, “Airborne EW (EA) Systems and Components Forecast 2012-2022,” predicts a future shift towards reestablishing airborne EW capabilities that counter anti-access, area-denial systems will translate into spending on airborne EW systems—accounting for over 35 percent of this global spending.
Key features of the secure boot SRAM FPGA reference design include:
− SmartFusion2 security uniquely qualifies it as root-of-trust
− Mitigates DPA/SPA configuration vulnerabilities of large SRAM FPGAs where anti-tamper is required
− Minimal impact to existing system architecture
− Licensed physically unclonable function (PUF) technology from Instrincic-ID allows for unique binding to a target component
− Only requires a simple user eligibility certification to use DPA patents licensed by Microsemi from Cryptography Research